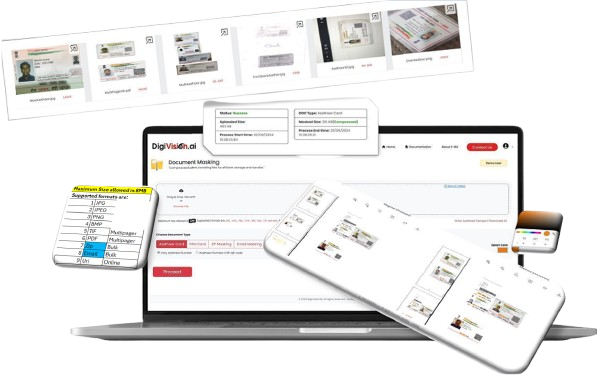
Secure On-Premises Aadhaar Masking Solution
On-Premises PII-Masking
(Complete Data Protection)
Comparison between On Prem and Cloud
| Criteria | On-premise | Cloud |
|---|---|---|
| Data Security | Full control, customizable security policies, reduced external threats | Cloud provider security, shared responsibility, potential exposure |
| Compliance and Regulations | Ensures full data residency compliance, easier audits | Data residency offered, but requires verification, evolving regulations |
| Scalability | Limited by hardware, requires time and CapEx for scaling | Elastic scaling on-demand, pay-as-you-go model |
| Cost Structure | High initial CapEx, predictable long-term operational costs | Low upfront cost, OpEx model, potential for cost overruns based on usage |
| Performance & Latency | Low latency for local systems, ideal for real-time transactions | Potential for latency due to internet dependency, but optimized by provider |
| Customization | Fully customizable, complete control over updates and software | Limited customization, provider-controlled updates and features |
| Business Continuity & Disaster Recovery | Requires investment in redundancy, vulnerable to local disasters | Built-in disaster recovery, resilience across multiple regions |
| Maintenance & Expertise | In-house IT team required, more complex maintenance | Managed services, lower IT overhead, faster access to innovations |
| Data Privacy & Confidentiality | Highest control over data, reduced external access risks | Risk of third-party access, advanced encryption options available |
| Integration with Legacy Systems | Easier integration with existing infrastructure and legacy systems | Potential challenges with legacy systems, requires cloud-specific adaptations |
| Initial Setup Time | Longer setup time due to hardware procurement and installation | Quick setup with cloud resources, fast provisioning |
| Vendor Lock-in Risk | No lock-in but high CapEx on infrastructure | Possible cloud vendor lock-in due to proprietary services and platforms |

DigiDrive.AI
Making Paradigmatic Shift in Document Management